I’ve been meaning to write a new post about Azure Backup for a while, and with the recent general availability announcements of several features, now seems like the perfect time.
Azure Backup is a very mature Azure service at this point but I think there are a lot of people out there who may be using this service but who are not aware of all the latest features it has to offer.
This post will cover some select new features that have become generally available (GA) over the past year or so. I’ll discuss what these features are and why you might want to consider using them.
Enhanced soft delete for Azure Backup (GA since October 2023)
Let’s start with the most recent announcements, which include an enhanced soft delete configuration. This is a feature for both Recovery Services Vaults and Backup Vaults. I’ve blogged previously about the difference between those two resources here.
Soft delete itself is not a new feature and is there as a safety measure to protect against both accidental and malicious deletion. The concept is simple, if your backup data is deleted then it can still be recovered for up to 14 days while it is held in a soft delete state. This itself is a great feature and what’s more those 14 days of soft delete retention are provided free of charge.

Two noteworthy new additions to this feature include firstly, the soft delete retention period can now be extended up to a maximum of 180 days. Note, anything beyond the default 14 day retention will be chargeable.
Secondly and importantly, you can set your soft deletion to an ‘always-on‘ state. Previously, it was possible to disable the soft delete feature and purge this backup data. Now, you have the option to make your soft deletion data immutable for the duration of the soft delete retention period that you have defined.
For example, if you specify a 30-day soft delete period then you will have to wait 30 days for these soft deleted backups to be purged automatically, there is no way to manually delete them or to override this setting with the always-on state enabled.
Since this action is irreversible, it’s crucial to consider the potential cost implications of committing to a lengthy retention period that you cannot later change.
Use cases: All customers should use the default 14 day soft delete feature as a minimum. It costs you nothing so is a “no brainer”. I would recommend to enable the always-on state for this 14 days as an extra security layer to protect your backups against malicious attacks and bad actors who may target your backup data and at least keep these most recent backups recoverable for that two week period.
For more heavily regulated organisations you will want to make sure that you have immutable backups of some description so that could be this feature or the vault level feature (more on this later) or you could use both.
Multi-user authorisation for Backup vaults (GA since October 2023)
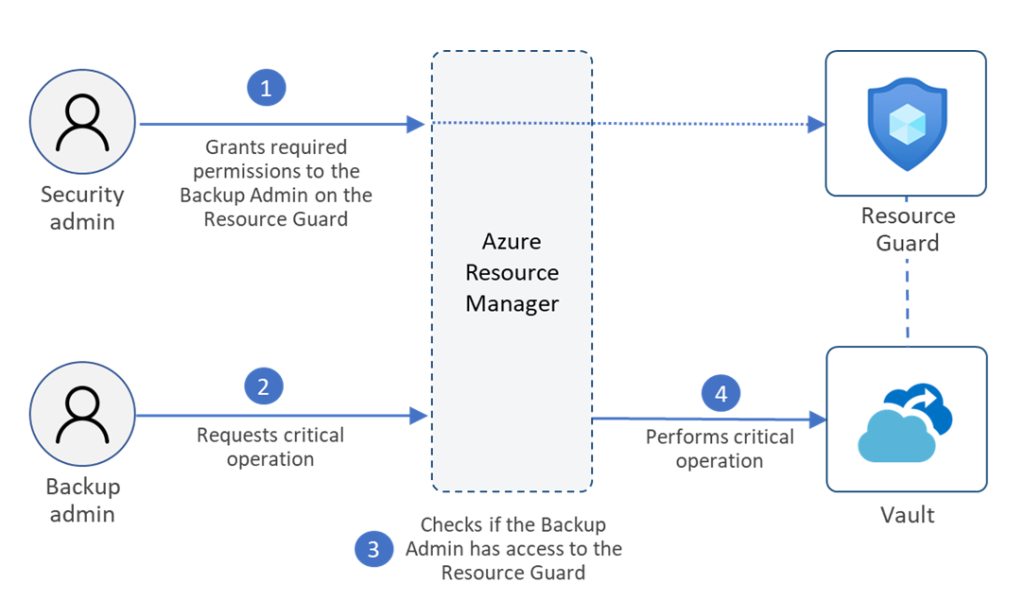
This is another feature that has recently gone GA for both Recovery Service Vaults and Backup Vaults. Multi-user authorisation (MUA) adds a Resource Guard (which is an Azure resource) as an additional layer of protection for privileged operations on your backups. These privileged operations require approval from a user that has access to the resource guard. Such privileged operations might include the likes of disabling soft delete, reducing backup retention periods or even deleting backup data.
The concept here is that a general backup operator has limited privileges on the vault and must request elevated permissions from another user who has access to the Resource Guard which ideally is stored on a separate Azure subscription or even another tenant for maximum isolation.
Typically, Privileged Identity Management (PIM) would be the service that is utilised to request and approve the privileged and time-bound permissions required for the protected operation.
Use cases: This feature essentially adds another layer on top of PIM. If you are already following a least privileged access model then you likely have PIM in place already.
This new feature allows you to get a bit more granular and to choose which critical tasks within Azure Backup that you want to lock down to requiring MUA. Very useful in a heavily regulated customer environment.
Cross Subscription Restore for Azure Virtual Machines (GA since August 2023)
This one is relatively self-explanatory. We can already restore Azure virtual machines to different availability zones and different Azure regions but with this feature you can now also restore an Azure VM backup to a different Azure subscription on your tenant. This feature is enabled by default on Recovery Services Vaults and Backup Vaults but can be disabled if required.
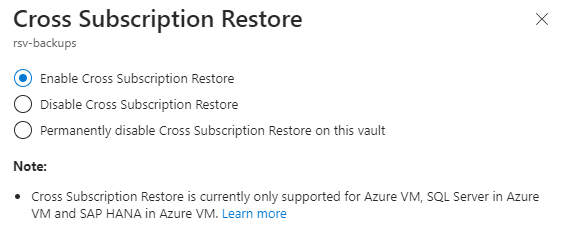
Use cases: The primary use case here is if you want to restore a virtual machine into a different environment, e.g. test to production or production to test.
More useful than you might realise!
Multiple backups per day for Azure Virtual Machines (GA since June 2023)
This a big one. For years, Azure virtual machine backups were limited to a single recovery point objective (RPO) per day but we can now have full Azure virtual machine backups as often as every four hours.
This feature is only supported in the newer enhanced backup policy type.
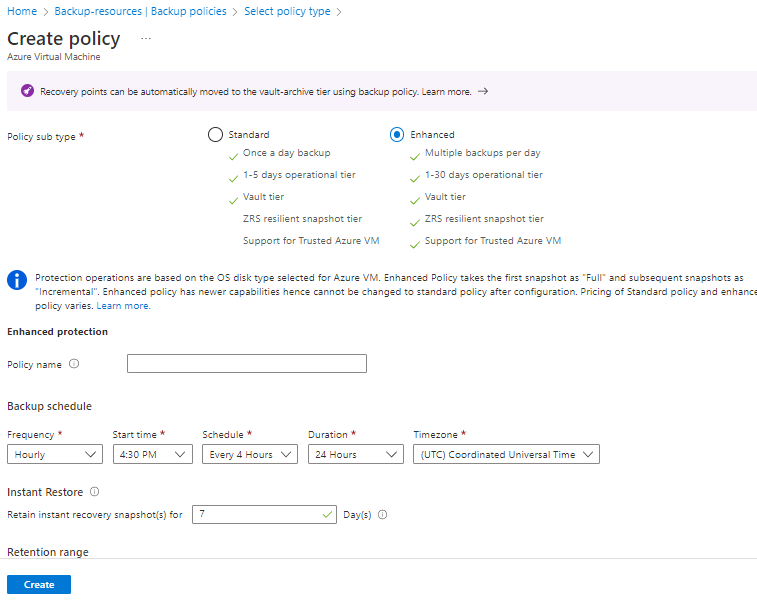
Use cases: A fairly obvious use case here, where you need more RPOs than once per day for your workloads. Losing up to a full 24 hours of data can be detrimental to some businesses. Therefore, the ability to restore your data as close as possible to the incident that necessitated data restoration is crucial.
Immutable vault for Azure Backup (GA since March 2023)
This feature allows you to protect the data in your entire Recovery Services Vault or Backup Vault from deletion. It is a setting applied at the vault level rather than to individual backups. The concept here is to prevent deletion (accidental or otherwise) of your retained backup data. This setting can be set to a status of enabled (which can be disabled by a privileged user) or enabled and locked which is a permanent setting that can’t be deactivated. With the vault in a locked state it is not possible to delete backup data or to reduce the retention period. This is very similar to the ‘always-on’ state for soft delete that I mentioned earlier.
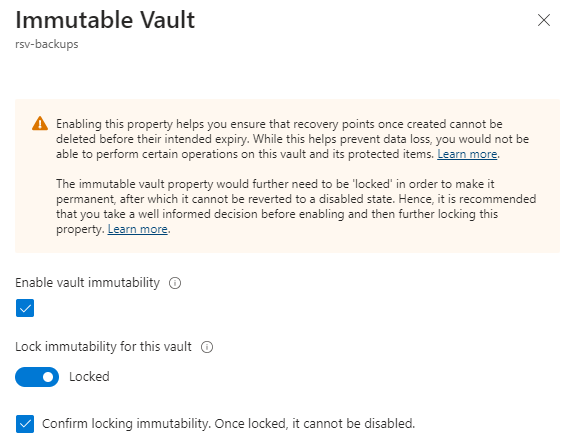
Use cases: Immutable backups are often a requirement for highly regulated organisations and the lock feature allows you to make this setting permanent and effectively tamperproof. Just remember the cost implications if you are committing to long term backup retention periods that cannot be changed later.
Smart tiering to vault-archive tier for Azure Backup (GA since October 2022)
This feature has been around for over a year now but might be something that many have not used before or may not even be aware of. Azure Backup has support for an archive tier of blob storage which is ideal for long term backup data retention. There are specific requirements here for (non-SQL) Azure Virtual Machines such as only monthly and yearly RPOs are supported and the backup data must have spent at least 3 months in the backup vault and have at least 6 months remaining in its retention period.
As Azure Backup uses incremental recovery points, we need to convert these to full size recovery points if using the archive tier. Therefore, we are storing larger backup points albeit at a lower storage cost.
Depending on the total size and daily churn rate of your data, this may negate the benefit of utilising this feature as for low churn rate data, the cost implications of converting to a full backup and moving that to the archive tier can in some cases actually cost more money overall.
Azure Backup has a great recommendation feature that will analyse your backup data and suggest where using the backup tier will provide overall cost savings. As there is some work involved in moving data between these backup tiers, Azure has a useful feature called smart tiering.
By enabling this feature, you can put Azure Backup in control and automatically move your backups to the archive tier either based on those recommendations or else move after a set number of months that you decide (minimum of 3 months).
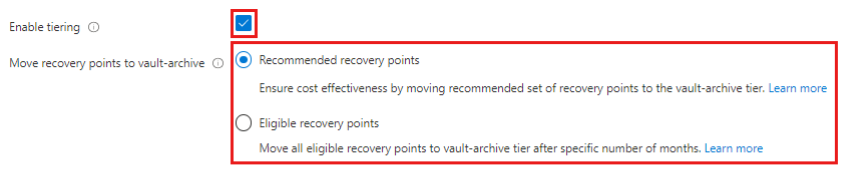
Use cases: This feature is really for customers who need long-term data retention for high churn workloads especially where there are a lot of monthly backups going back over several years. The savings are on the blob storage costs of the backup data.
and there’s more…
Here’s a couple of bonus items that have recently been announced and are in Public Preview at the time of writing.
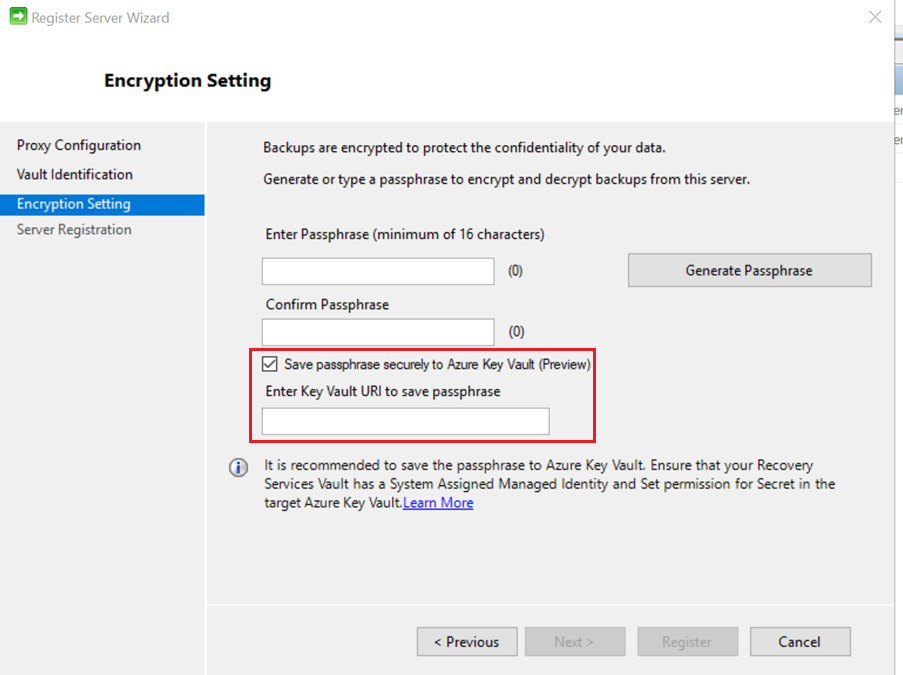
Save Azure Backup Recovery Services Agent (MARS) passphrase to Azure Key Vault (currently in Public Preview)
This is a great new feature for the MARS Azure Backup service. Primarily, I see deployments of MARS for files/folder backup of on premises Windows servers to Azure. One of the features of this service is that it generates a passphrase which is used to encrypt the backup data. This passphrase needs to be kept secure and if lost, even Microsoft support can’t help you. I’ve seen far too many instances where this passphrase was lost and on at least one occasion where a server crashed and the only copy of this passphrase was stored on that same server!
Now, when registering your MARS backup server, you have the option to securely store the passphrase directly in an Azure Key Vault. No more worrying about lost passwords. Please do this!
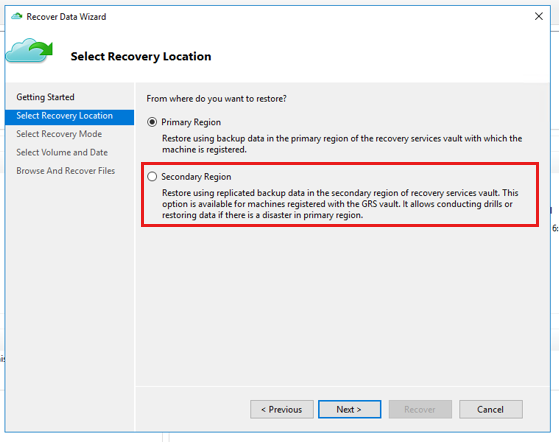
Cross Region Restore for MARS Agent (currently in Public Preview)
Finally, another nice feature for those MARS on premises backups stored in Azure is the ability to restore from a paired region. Previously, this was only possible if you had geo-replicated your data and Azure had declared a regional outage. Now, it is possible to restore directly from the paired region at any time.
This feature must be enabled on the Recovery Services Vault and the trade off of being able to choose the region you wish to restore from at any time is that the data will be stored at the higher RA-GRS per GB rate.

Thanks Alan for this blog post. I fail to understand what always on soft delete brings additionally if immutability is enabled and locked. Do you have a clear view on this please?
LikeLike